Welcome back to my walkthrough of hackthissite.org’s CTF missions. I will be going through my thought process of how I solved these missions, and therefore also giving away the solutions. If you came across this to give you hints, watch out for spoilers! Good luck, have fun.
Our next realistic mission has three objectives for us to complete:
- Find the account of Gary Hunter.
- Move the $10,000,000 [that are in his bank account] into the account dropCash [seems to be the username of the account].
- Clear The Logs, They’re held in the folder ‘logFiles’.
Firstly, I will begin to look around the website and see what I can find in terms of forms, redirects, and cookies that are used. Futhermore, I will also make an account to ensure I capture as much as possible with this first initial investigation. The following image demonstrates a quick explanation on the implementation of some of the functionality in this website:
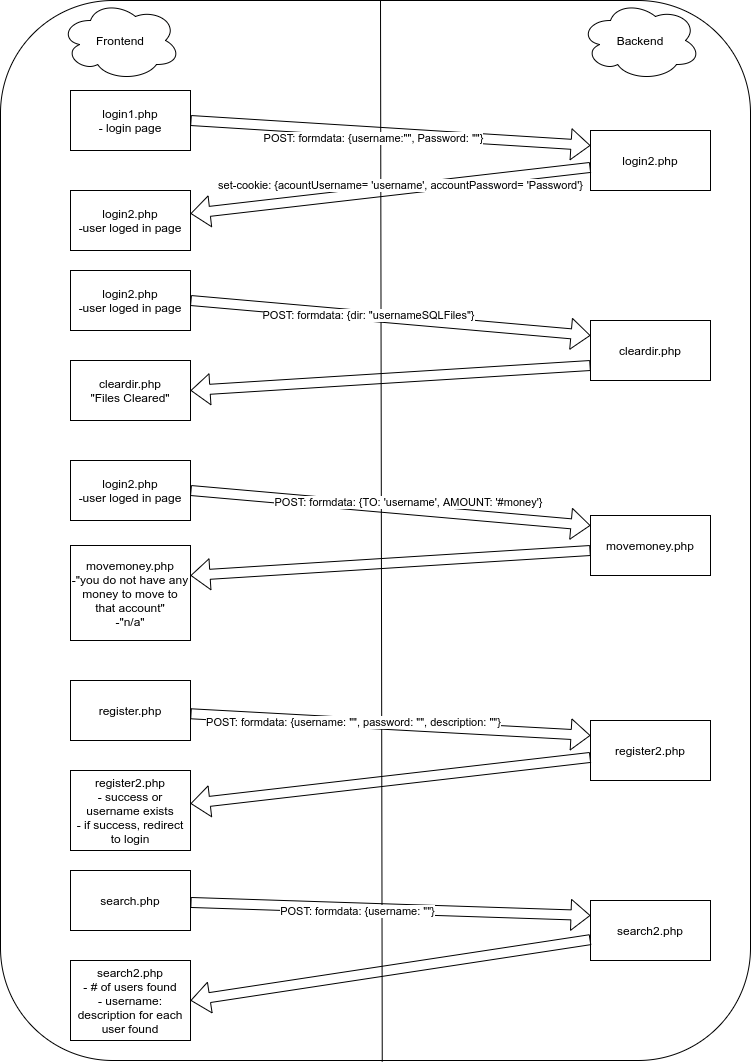
Now that I have a better understanding of the implementation of this website, I will now pivot my attention back to the targets of this challenge. My first step is to handle objective 1: “Find the account of Gary Hunter”. This is essential in order to complete objective 2. The first thing that would come to mind to find the account of this character, would be to use the ‘User Info’ webpage to find the account details. This is shown by the ‘search.php’ flow in the diagram above. I will begin by doing searches for common usernames that are similar to the name ‘Gary Hunter’. The following table shows my results:
| username | description |
|---|---|
| garyhunter | kajfajkfawefae |
| GaryHunter | a |
| garyHunter | |
| Garyhunter | 1234543 |
| gaRyhunter |
Trying to login using the few obvious ones, we instantly cross off the following usernames as being the account that I am meant to target as the amount of money within these accounts are not 10 million: {Garyhunter, GaryHunter}. Since I don’t know whether it may even be one of these accounts that I have just outlined, I will revist the user info page. This time, my goal is to somehow see if I can extract an entire user list of their database. The only way that this would be possible is if the input to the form on this webpage is not properly sanitized and SQL injection is possible. I will try the go-to ' OR 'a'='a as the username. Which did in turn return the entire user list of their database. Now to find the target account username. Unfortunately, there are numerous accounts in this list that seem to be previous attempts at completing this challenge, some of which suggest that ‘this is the secret account of gary hunter’. Since it’s unclear which account is the one that we are meant to move forward with, I will consult a forum. The forums suggest that we are looking for the username: GaryWilliamHunter. Thus we can simply change our search for that username. Finally, I have the username and description of the account that I am meant to target: GaryWilliamHunter : -- $$$$$ --. I’m not aware whether the accounts that claimed to be the secret account would have worked, but for the purpose of this challenge I would assume that these were made maliciously after the fact by other users that tried to complete this challenge.
Now I will shift my focus to the second objective, moving 10 million from the account GaryWilliamHunter to the account dropCash. In order to do so, I will login with my account and try to deduce how the backend processes a money transfer request. From my previous investigation, the user must enter the account name to which they wish to transfer to, and the amount that they wish to transfer. This is outlined in the flow diagram above. There is no hidden field that sets from which account the request originates, thus this must be deduced by the cookies that are set once you login. I already know that once you login, two cookies are set: accountUsername and accountPassword, and both are stored in clear. Now, this is a terrible idea from an implementation point of view as it leaves requests possible to tampering. In practice, these two cookies should be replaced by some hashed session ID that makes it incredibly hard to impersonate another user. My first plan of action is to determine whether both of these cookies are used in order to validate a money transfer request. I will do so by unsetting the accountPassword cookie manually whilst loged in, and attempt to transfer $0 to GaryWilliamHunter. If the request passes validation I expect a message saying something along the lines of ‘not enough money to complete transfer’. This indeed did turn out as expected. This suggests that, if I were to change the cookie accountUsername to GaryWilliamHunter, and simply send $10,000,000 to the account dropCash then this objective would be complete. Voila! I have received a message saying : “Congratulations, 1st Objective Done, Now Cover Your Tracks”.
Finally, I move onto the last objective. From my previous investigation, the method to complete this is quite simple. I will begin by once again loging in to my account. The functionality “clear files in personal folder” has a hidden input of which directory to target for deletion. If I were to change this field to target logFiles then I expect to complete this objective. All that needs to be done is press the button.
Voila! I have now completed this mission. On to the next.